Astuce: HashiCorp Learn propose également un guide constamment mis à jour pour injecter des secrets dans les pods Kubernetes via le Vault Helm Sidecar. Visitez cette page pour les étapes les plus récentes et des exemples de code.
Kubernetes, HashiCorp Vault , Vault. vault-k8s, Kubernetes Mutating Admission Webhook Init Sidecar .
, , API Vault.
:
Init . , job , .
Init Sidecar. Init , Sidecar, (sidecar , , ). , , .
Kubernetes Vault Policy. , , , Pod , . .
Vault Agent, consul-template. , Vault , ..
Kubernetes Vault . , What's Next for Vault and Kubernetes.
, Vault Kubernetes init sidecar , , . Vault-k8s Vault Helm Chart ( , ). , .
- Vault Helm Chart, vault-k8s (. ). Docker , vault-k8s , Helm. Vault Helm Chart, , , .
Helm Chart, , Vault, vault-k8s, Kubernetes Mutating Admission Webhook ( namespace). , webhook vault-k8s Kubernetes API.
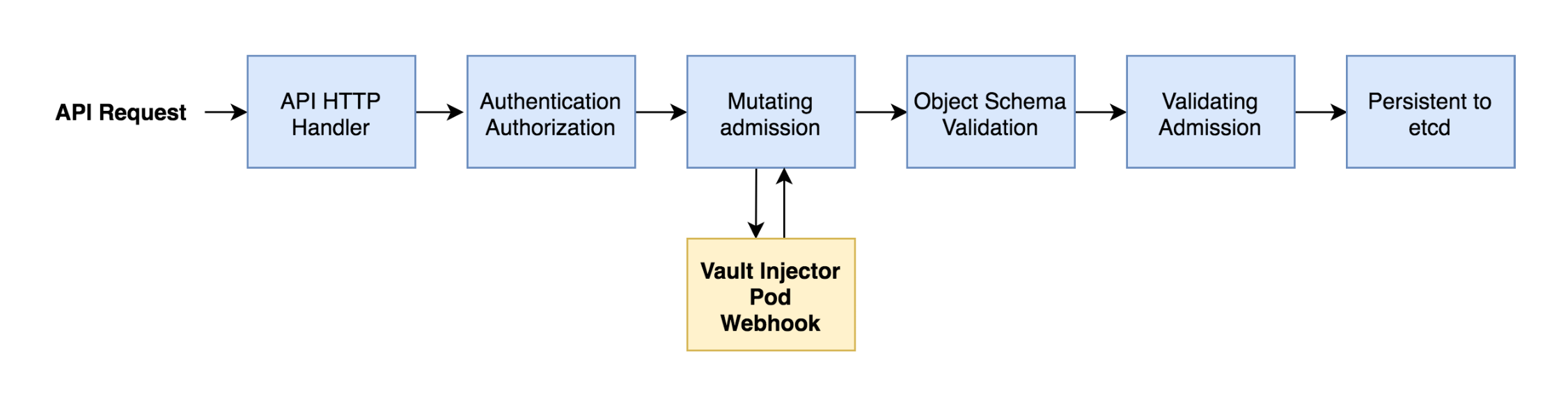
Vault, . , webhook vault-k8s , , ( ). , , . namespace, , Kubernetes Service Accounts, Vautl Policy, , .
, Vault ? , , , Vault. kubectl patch Pod, webhook vault-k8s, init sidecar ( , Service Account Vault Policy).
# patch-basic-annotations.yaml
spec:
template:
metadata:
annotations:
vault.hashicorp.com/agent-inject: "true"
vault.hashicorp.com/agent-inject-secret-helloworld: "secrets/helloworld"
vault.hashicorp.com/role: "myapp"
, vault-k8s init sidecar Pod, secret/helloworld Vault, /vault/secrets/helloworld, "myapp" .
, vault-k8s . , Vault Helm Chart. , Sidecar, Vault, - webhook vault-k8s Kubernetes Mutating Admission Webhook.
Vault, , Vault Helm Chart values.yaml.
injector:
enabled: true
namespace, Vault Helm Chart.
kubectl create namespace demo
kubectl config set-context --current --namespace=demo
helm install --name=vault \
--set='server.dev.enabled=true' \
./vault-helm
, Vault "app" . , , , .
kubectl exec -ti vault-0 /bin/sh
cat < /home/vault/app-policy.hcl
path "secret*" {
capabilities = ["read"]
}
EOF
vault policy write app /home/vault/app-policy.hcl
Vault Kubernetes Auth service account ( ).
vault auth enable kubernetes
vault write auth/kubernetes/config \
token_reviewer_jwt="$(cat /var/run/secrets/kubernetes.io/serviceaccount/token)" \
kubernetes_host=https://${KUBERNETES_PORT_443_TCP_ADDR}:443 \
kubernetes_ca_cert=@/var/run/secrets/kubernetes.io/serviceaccount/ca.crt
vault write auth/kubernetes/role/myapp \
bound_service_account_names=app \
bound_service_account_namespaces=demo \
policies=app \
ttl=1h
, Vault KV Secrets Engine. - pod, Vault.
vault kv put secret/helloworld username=foobaruser password=foobarbazpass
app.yaml . -, . Service Account, Vault Policy, . , .
# app.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: app
labels:
app: vault-agent-demo
spec:
selector:
matchLabels:
app: vault-agent-demo
replicas: 1
template:
metadata:
annotations:
labels:
app: vault-agent-demo
spec:
serviceAccountName: app
containers:
- name: app
image: jweissig/app:0.0.1
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: app
labels:
app: vault-agent-demo
service account. , /vault/secrets .
kubectl create -f app.yaml
kubectl exec -ti app-XXXXXXXXX -c app -- ls -l /vault/secrets
, pod , , / .
# patch-basic-annotations.yaml
spec:
template:
metadata:
annotations:
vault.hashicorp.com/agent-inject: "true"
vault.hashicorp.com/agent-inject-secret-helloworld: "secret/helloworld"
vault.hashicorp.com/role: "myapp"
.
kubectl patch deployment app --patch "$(cat patch-basic-annotations.yaml)"
kubectl exec -ti app-XXXXXXXXX -c app -- cat /vault/secrets/helloworld
, tmpfs mount /vault/secrets helloworld . : , webhook vault-k8s Pod, Init- , Vault Agent Sidecar .
, , , /vault/secrets/helloworld , Go . , , , . ?
data: map[password:foobarbazpass username:foobaruser]
metadata: map[created_time:2019-12-16T01:01:58.869828167Z deletion_time: destroyed:false version:1]
, Vault Agent Templates, . postgresql. , , ( ) ..
# patch-template-annotations.yaml
spec:
template:
metadata:
annotations:
vault.hashicorp.com/agent-inject: "true"
vault.hashicorp.com/agent-inject-status: "update"
vault.hashicorp.com/agent-inject-secret-helloworld: "secret/helloworld"
vault.hashicorp.com/agent-inject-template-helloworld: |
{{- with secret "secret/helloworld" -}}
postgresql://{{ .Data.data.username }}:{{ .Data.data.password }}@postgres:5432/wizard
{{- end }}
vault.hashicorp.com/role: "myapp"
, , .
kubectl patch deployment app --patch "$(cat patch-template-annotations.yaml)"
kubectl exec -ti app-XXXXXXXXX -c app -- cat /vault/secrets/helloworld
:
postgresql://foobaruser:foobarbazpass@postgres:5432/wizard
, Vault. , .
vault-k8s GitHub. , , Agent Sidecar Injector Injecting Vault Secrets Into Kubernetes Pods via a Sidecar. HashiCorp Learn , .
:
, - :
HashiCorp Vault: Delivering Secrets with Kubernetes
Kubernetes Traffic Ingress with HashiCorp Vault PKIaaS and JetStack Cert-Manager
Mutual Auto-Unseal Two Vault clusters in Kubernetes